Are Multi-Factor Authentication (MFA) Solutions Equally Secure?
Happy Beginning
US National Institute of Standards and Technology (NIST) tells us that stopping all online crime is not a realistic goal, but simple steps can massively reduce the likelihood you’ll be the next victim. It’s simple: turn on MFA today! [1]
What is MFA then?
The intent of multi-factor authentication (MFA) is to provide a higher degree of assurance of the identity of the individual attempting to access a resource, such as physical location, computing device, network or a database. MFA creates a multi-layered mechanism that an unauthorized user would have to defeat in order to gain access. [2]
Authentication Factors
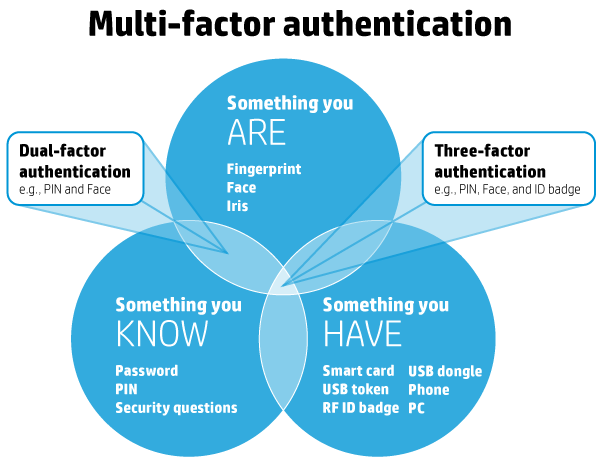
The overall authentication process for MFA requires at least two of the three authentication methods described in PCI DSS Requirement 8.2:
a) Something you know, such as a password or passphrase. This method involves verification of information that a user provides, such as a password/passphrase, PIN, or the answers to secret questions (challenge-response).
b) Something you have, such as a token device or smartcard. This method involves verification of a specific item a user has in their possession, such as a physical or logical security token, a one-time password (OTP) token, a key fob, an employee access card, or a phone’s SIM card. For mobile authentication, a smartphone often provides the possession factor in conjunction with an OTP app or a cryptographic material (i.e., certificate or a key) residing on the device.
c) Something you are, such as a biometric. This method involves verification of characteristics inherent to the individual, such as via retina scans, iris scans, fingerprint scans, finger vein scans, facial recognition, voice recognition, hand geometry, and even earlobe geometry.
Independence of Authentication Mechanisms
The authentication mechanisms used for MFA should be independent of one another such that access to one factor does not grant access to any other factor, and the compromise of any one factor does not affect the integrity or confidentiality of any other factor. For example, if the same set of credentials (e.g., username/password) is used as an authentication factor and also for gaining access to an e-mail account where a secondary factor (e.g., one-time password) is sent, these factors are not independent. Similarly, a software certificate stored on a laptop (something you have) that is protected by the same set of credentials used to log in to the laptop (something you know) may not provide independence. [2]
Cyber Attacks that Break MFA
1) Key Logging and Redirection
The keystroke logger permits an attacker to monitor your typing to retrieve login credentials (typically username/password). Two-factor authentication is typically effective against these passive attacks, since they include a one-time password component obtained from the device (e.g., hardware token or phone). However, malware could also redirect some of those keystrokes to an attacker, whom you have just enabled to log in as you.
2) Man-in-the-middle Attack
Network-based man-in-the-middle (MITM) attacks are typically dealt with by cryptographic network protocols (SSL/TLS). However, forgery of fraudulent cryptographic certificates, while relatively rare, has shown flaws in this dependency. This can be accomplished by injecting fake root certificates in the browser’s trusted certificate database, or by compromising any of the many root certificate authorities already listed there. If an attacker is able to become an undetected intermediary, they can perform all of the capabilities of the key logging and redirection threat, but with less presence (and detectability) on the user’s computer.
3) Man-in-the-browser Attack
Sophisticated malware known as a man-in the-browser – such as Zeus – allows an attacker to falsify a user’s browser display, making the user think that the website is doing what they intend while actually it is doing something completely different, directed by an attacker. The best countermeasure for this is the use of a two-factor technology that independently and securely displays to the user the nature of a transaction being approved. Ideally, this independent display would be on a different device using an independent communications channel.
4) Account Recovery
You also need to consider what happens if you lose one of your authentication factors (or if an attacker pretends to). If the response is to temporarily disable two-factor authentication, then an attacker might be able to social engineer the account recovery process to get access to the account. Worse yet, if you’re using knowledge-based authentication (“What was the name of your first pet?”) for account recovery, these answers are often very easy for an attacker to guess and provide much worse security. Remember that the attacker will pick whatever is the weakest point in your authentication system to attack. It was account recovery more than the lack of two-factor authentication that exposed Mat Honan of Wired Magazine to a widely reported and devastating attack last year.
5) Third Party Risks
Some two-factor authentication systems rely on third parties for the issuance, verification, or communication with verification of physical tokens. The vulnerabilities inherited from third parties are best illustrated by the breach of RSA’s SecurID authentication system in 2011. Although the extent of the RSA breach isn’t fully known, it is thought that the attackers could have gotten access to information to create counterfeit tokens.
Authentication using SMS text messaging and other telephony-related means is dependent on the mobile carrier’s practices for assigning and reusing phone numbers. If an attacker can convince the carrier that they are the user and they lost their phone and need a new one, they would be in a position to intercept text messages and phone calls, providing the second authentication factor. This has led to a request from some Australian telecoms that banks not use SMS for two-factor authentication.
6) Social Engineering Attack
The ultimate dependence of MFA is "You" - Something YOU Know, Something YOU Have and Something YOU are. The use of social engineering attacks on human weakness is a major attack vector to compromise MFA.
Stricter independence controls in MFA and more user awareness trainings are the key.
Strict Independence in MFA is Good
Stricter the independence elements in MFA the better.
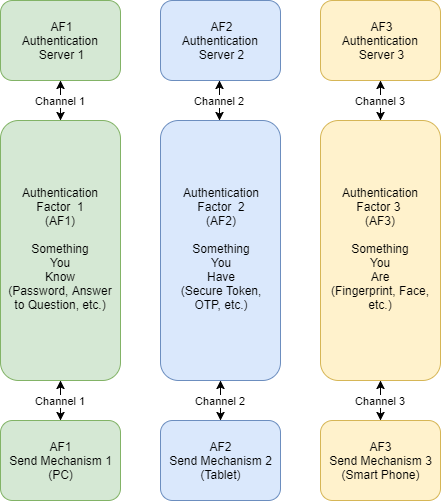
The basics of strict independence in MFA are that:
a) Independent MFA Clients – they are to send authentication factors:
Passwords – Something You Know;
Secure Token & One-time Password – Something You Have;
Fingerprint & other biometrics – Something You are.
b) Independent Communication Channels
c) Independent MFA Servers
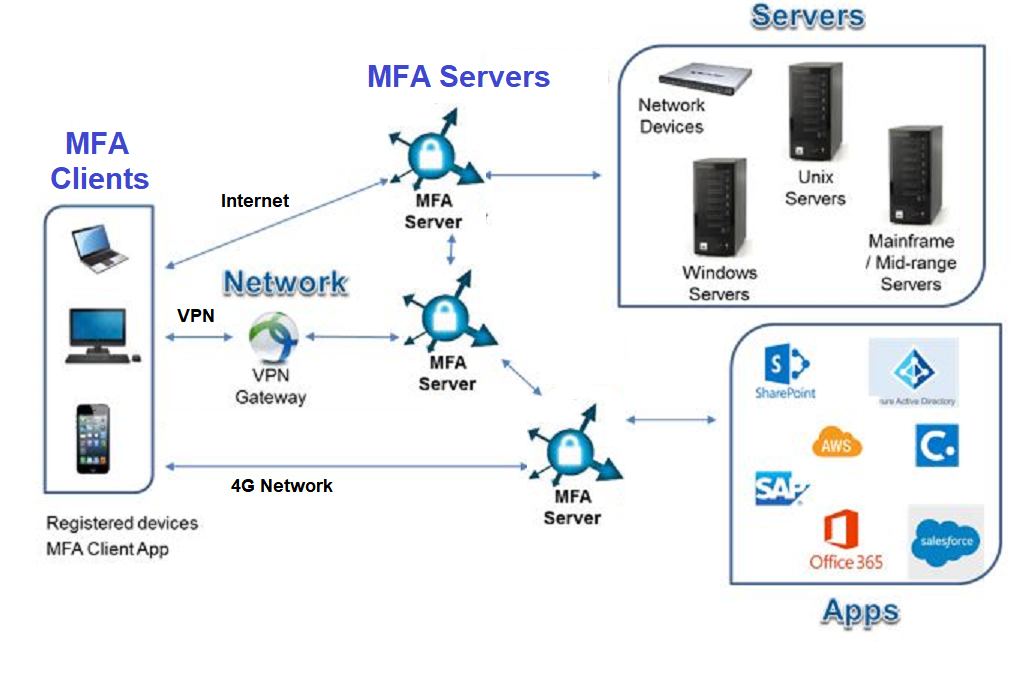
Conclusion
The strength of Multi-Factor Authentication depends on its degrees of independence in MFA clients, MFA channels, MFA servers and their interfaces. MFA solutions are not created equal. Watch out in MFA design and implementation.
References
[1] NIST on Back to basics: Multi-factor authentication (MFA)
https://www.nist.gov/itl/tig/back-basics-multi-factor-authentication
[2] PCI: Guidance for Multi-Factor Authentication v1.0, Feb 2017
https://www.pcisecuritystandards.org/pdfs/Multi-Factor-Authentication-Guidance-v1.pdf
[3] 5 Things to Consider with Multi-Factor Authentication
http://www.pathmaker-group.com/5-things-consider-multi-factor-authentication/
[4] https://www.itbusinessedge.com/slideshows/five-most-common-security-attacks-on-two-factor-authentication.html

