Simulated external and internal attacks to validate your security posture.
Penetration Testing is to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behavior. iSystems Consultant can customize our Penetration Test services to fit your business needs and IT environment. Through our test results your organization can better understand cybersecurity risks to your assets, business operations and growth. Our services include:
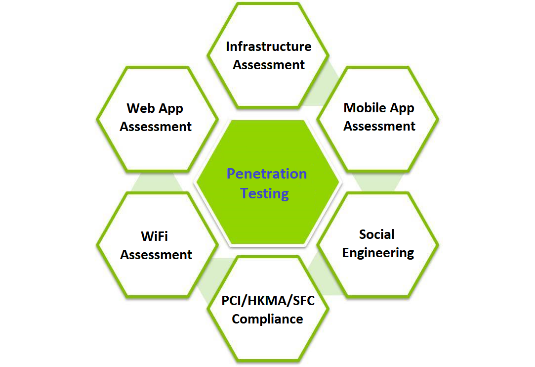
- Infrastructure Assessment – fully assess vulnerabilities in servers, network devices and IT systems
- Mobile App Assessment – comprehensively test the security of mobile devices and installed applications based on industry best practice of OSSTMM, OWASP, etc
- Social Engineering/Phishing Test – assess security awareness and general security controls with respect to human manipulation, including email, phone calls and physical access. We can support the language of the Phishing Test in English, Simplified Chinese & Traditional Chinese.
- PCI/HKMA/SFC Compliance Assessment
- WiFi Assessment – test the security of deployed wireless solutions, including the hotspots, controllers, etc.
- Web App Assessment – comprehensively test the websites
- Source Code Review – The Code Review can find out the bugs at early stage of the software development cycle.
Case Study : Penetration Test
Penetration test was successfully completed for a Hong Kong government department. The scope of the test covered IT infrastructure and web applications. An engagement letter was signed before the exercise which explained the roles and responsibilities of the client and the service provider. It also provided details on the penetration test timing, procedures and tool, attack vectors and evidence of system weaknesses. The penetration test was practical and tailor-made for the client; it involved more than basic press-the-button and checklist tasks. Our client can better understand its IT weaknesses and vulnerabilities before cyber crimes happen.
Key Benefits to our customers are:
We carry out network and system discovery with customized techniques for our clients. This is to find out technical "holes" in network and servers; it is very useful for practical technical improvements. The penetration test is practical and tailor-made for the client; it involves more than paper work and checklist. Our client can better understand its IT weaknesses and vulnerabilities before cyber crimes happen.
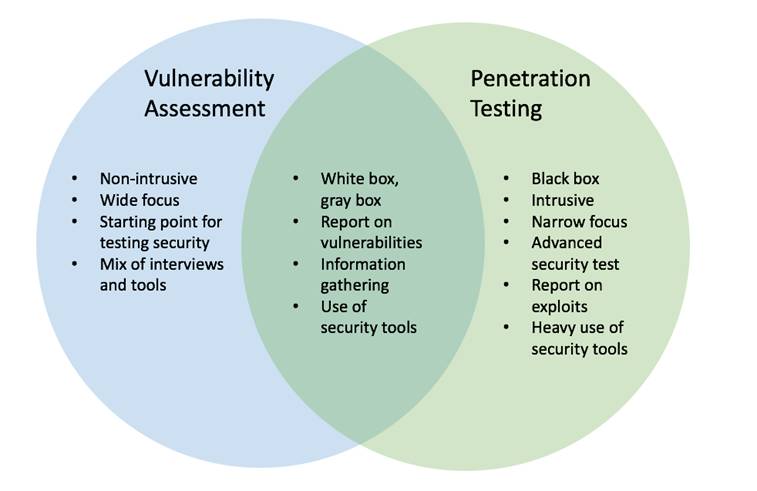
Vulnerability Assessment vs Penetration Test
The differences between vulnerability assessment and penetration testing show that both information security services are worth to be taken on board to guard network security. Vulnerability assessment is good for security maintenance, while penetration testing discovers real security weaknesses.