Discover Risk & Define appropriate mitigation strategies that fit your organization
Security Risk Assessment & Audit is to review and evaluate an organization's IT environment control and compliance on related technology, configurations policies, processes and procedures. It determines whether IT controls protect corporate assets, ensure data integrity and are aligned with the business's overall goals. iSystems Consultants examine not only physical security controls, but also overall business and financial controls that involve information technology systems. Services include:
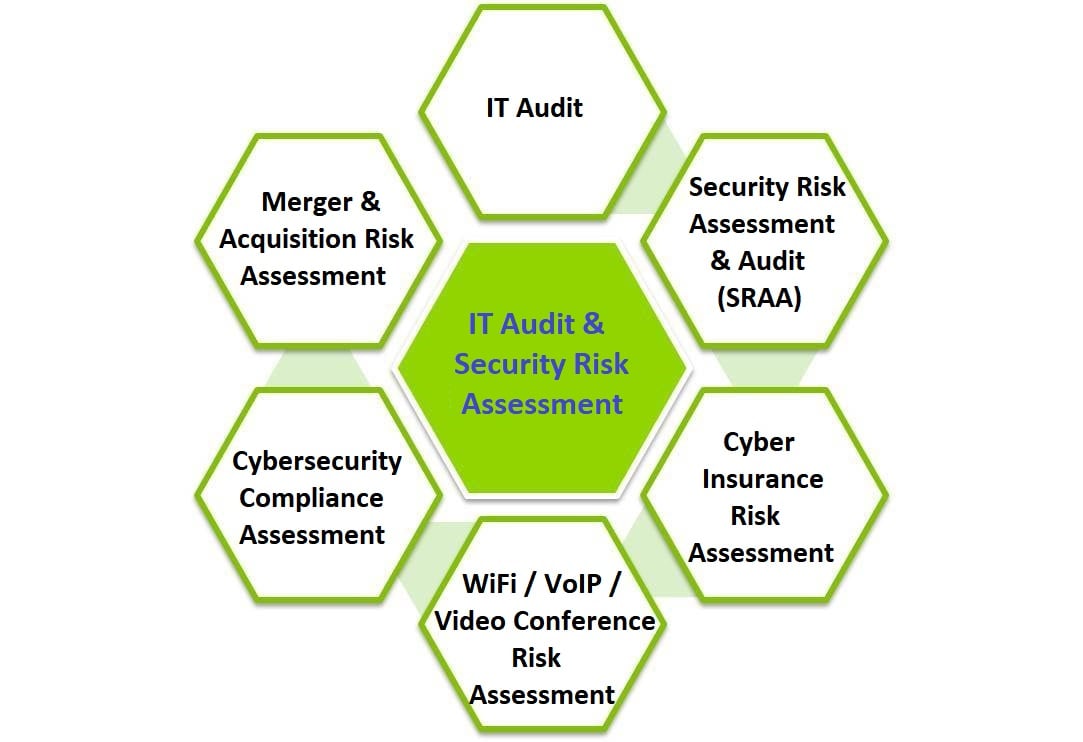
- IT Audit
- IT Security Risk Assessment
- Security Risk Assessment & Audit (SRAA) based on industry practices of ISO27001, HKSAR Government S17, G3, G51, etc
- Cyber Insurance Risk Assessment
- WiFi/VoIP/Video Conference Risk Assessment
- Cybersecurity Compliance Assessment
- Merger & Acquisition Risk Assessment
- Cloud Security Assessment
- IT Security Policy & Procedures Revision
- Compliance Audit Review based on HK Monetary Authority, Cyber-Resilience Assessment Framework, SFC Code of Conduct review etc.
Case Study - Network Audit
Network audit was performed for an established financial institution.
Main activities include:
- Network discovery and assessment of network architecture and topology,
- Network security assessment,
- Vulnerabilities and risk identification,
- Recommendations to management.
Network security review approach is based on ISO 27001. The network nodes consist of Extreme Black Diamond 10808, Summit X450 / X250 / 400 / 200; Juniper SSG550, ISG2000, IDP250, Juniper SSL VPN gateway SA2000
Key benefits to customers are:
- Early identification of infrastructure weaknesses and prompt improvements
- Maintenance of good company image
- Use of industry best practices on IT infrastructure and security approach
