When Journalist Under Cyber Attacks
In the Beginning
One chilly evening a quick-breathing voice muttered over the phone saying his laptop computer was sabotaged. As the story unfolded, a journalist John who reported in-depth news about a political figure has been warned to keep quiet. John continued his job as usual. Somehow one evening when John was too tired and slammed his laptop to the sleep mode. So was he. Early next morning when he got up, to his surprise, he found the wallpaper of his computer was replaced by a bloody chopped head’s theme. Five computer folders containing news stories and photos about the political figure went disappeared. John and his boss were keen to know how that happened and any traces on who did it.
This seemed like a typical cyber attack case that called for cybersecurity incident response handling. After the paper work on non-disclosure and service contract signed, Sam and Chole were assigned to investigate the incident. So far so good. John’s laptop was still in running state, and he didn’t want the investigation team to take away his computer. Sam dumped the memory information and run incident response tools to collected the key computer artifacts (computer objects of forensic interest).
Threat Hunting Journey
Back to the digital forensic laboratory, Sam and Chole split the job on analysis. Sam looked at memory dump analysis and Chole examined various logs and computer artifacts. They at first expected an easy catch on signs of malware download, email attachment execution, etc. After three days’ search, they found nothing. They looked at Prefetch and AmCache artifacts on program execution, Shellbags artifact on folder access, UserAssist artifact on program and shortcut access, MRU artifact on recently opened websites, folders and files, USB history artifact, Security & Application Event Logs. All to no avail. From these computer artifacts they could not find any Indicators of Compromise (IOC) on hacking activities or cyber attacks.

Sit Back and Reflect
Sam and Chole assumed the cyber attack worked through malware infection but there were no traces. What else? Sam asked Chole, “What went wrong here?” Chole calmly replied, “We are facing a sophisticated cyber actor. Think of the Diagram Model of Advanced Adversary and High Level of Capabilities, who may not even use malware to hack through remote control on the journalist’s laptop for sabotage.”
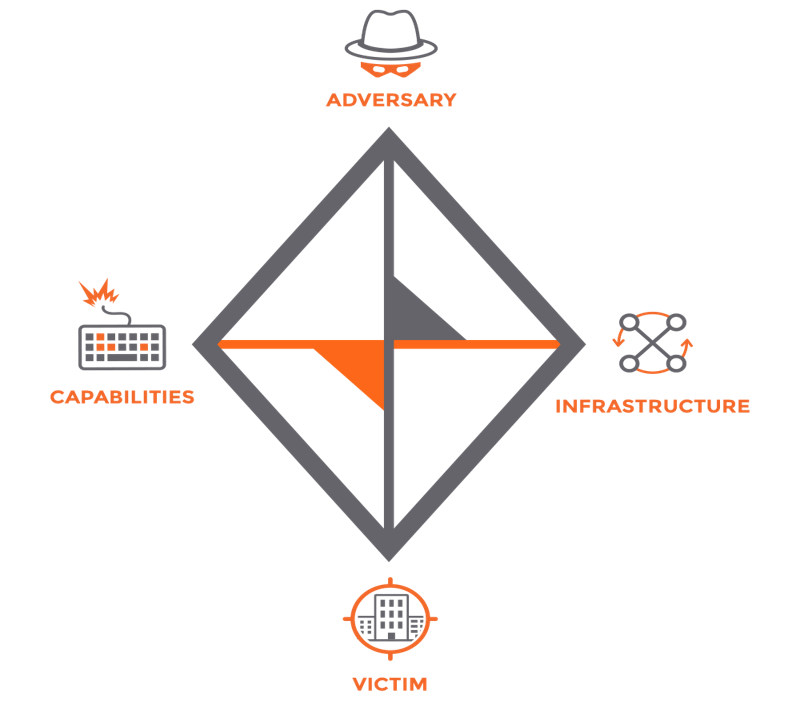
“Wow, this must be a fileless attack through PowerShell. I came across this piece of Cyber Threat Intelligence from Recorded Future.” Sam said with an exciting voice. PowerShell is part of Windows components, it is Windows’ DNA. Cyber attacks through PowerShell scripts can bypass many firewalls and antivirus solutions.
Sam and Chole hurriedly looked for PowerShell artifacts. Upon executing any PowerShell command or script, regardless if locally or through remoting, may write events to the following three logs:
• Windows PowerShell.evtx
• Microsoft-Windows-PowerShell%4Operational.evtx
• Microsoft-Windows-PowerShell%4Analytic.etl
Since PowerShell implements its remoting functionality through the Windows Remote Manage (WinRM) service, the following two event logs also capture remote PowerShell activity:
• Microsoft-Windows-WinRM%4Operational.evtx
• Microsoft-Windows-WinRM%4Analytic.etl
From there Sam and Chole got the clues. They did an anatomy of PowerShell cyber-attack scenario – how to generate the PowerShell script and how to deliver the script (payload) to the victim. The next step they did a timeline analysis by putting the events and time stamps together.
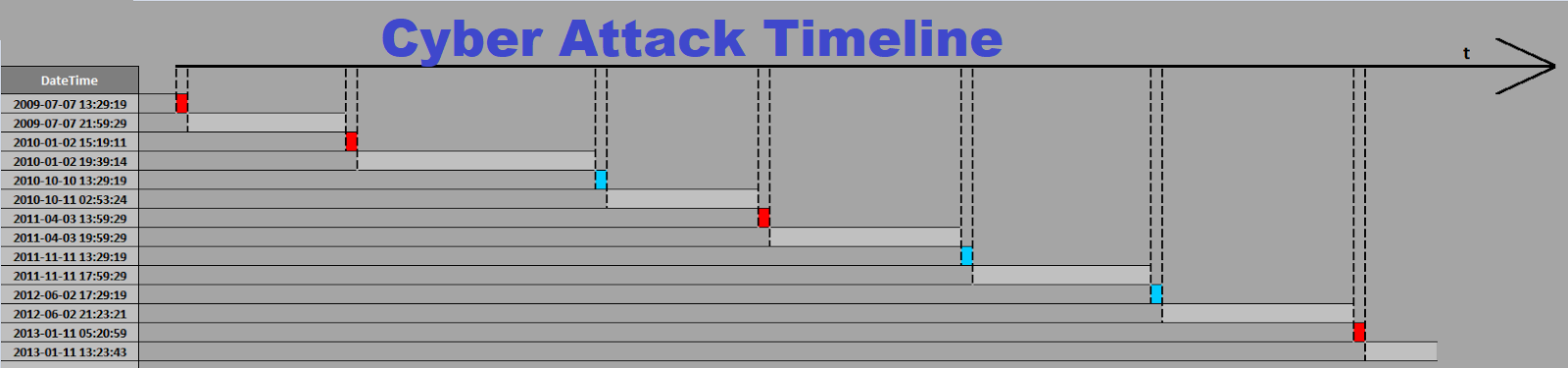
Postlude
Sam and Chole were relieved by now. Their humble wish was to tell John what happened and the source of cyber attack in order to pull him out of the dark. John smiled a little smile, and continued his job as usual. No fear, no regret.

