The ABC's of Cybersecurity Models
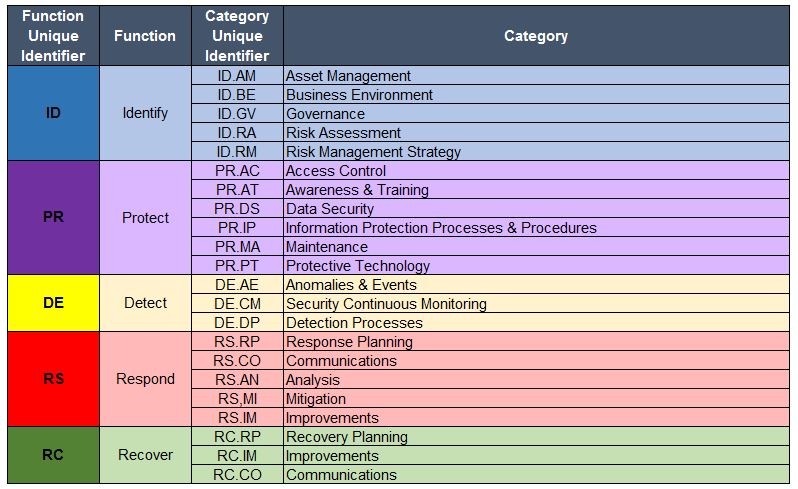
NIST Cybersecurity Framework
The Framework [1] focuses on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of the organization’s risk management processes.
The Framework Core consists of five concurrent and continuous Functions—Identify, Protect, Detect, Respond, Recover. When considered together, these Functions provide a high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk.
- Identify – Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect – Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
- Detect – Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
- Respond – Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.
- Recover – Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
The Basic Framework:
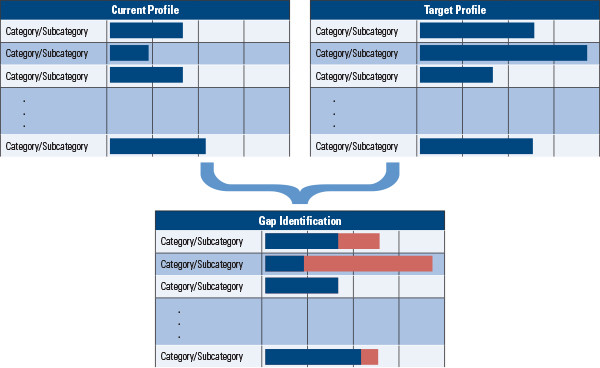
Gap Identification based on Current versus Target Profile:
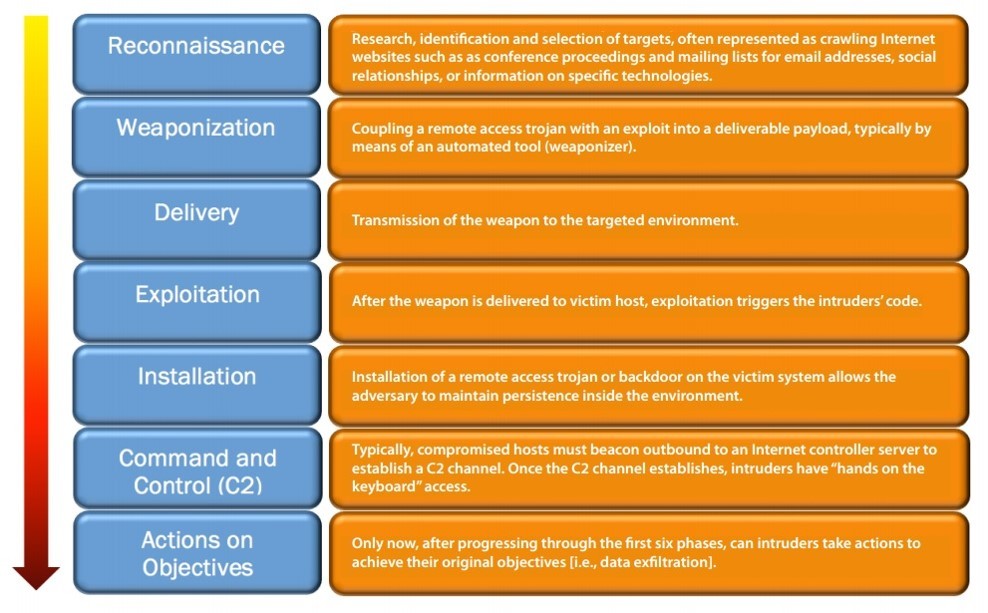
Lockheed Martin: Cyber Kill Chain
As attacks have become more advanced, the notion of a “Cyber Kill Chain” [2] has become common in cybersecurity discussions. This model is based on the premise that attacks have an operational life cycle to gather the information.
The model identifies what the adversaries must complete in order to achieve their objective. Stopping adversaries at any stage breaks the chain of attack.
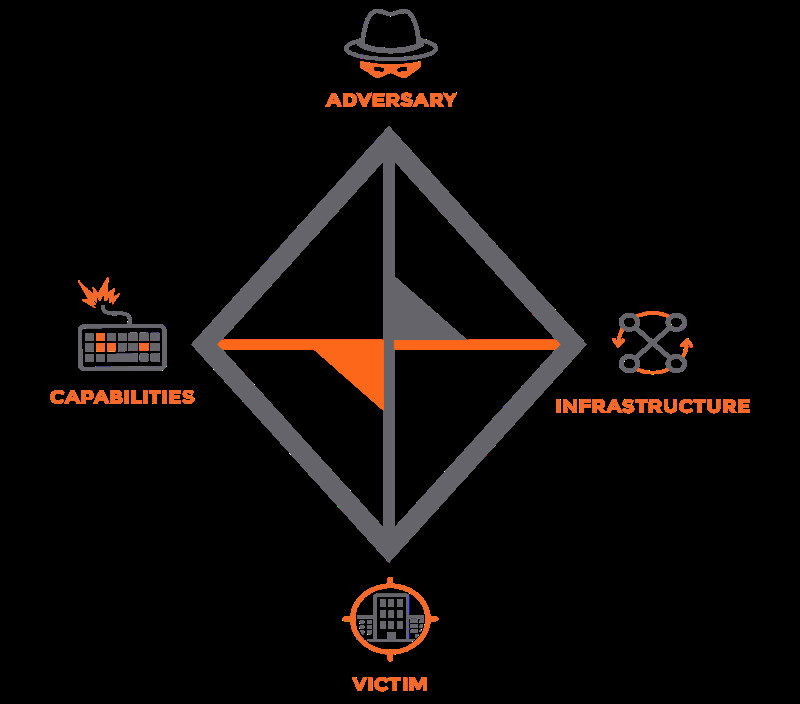
Diamond Model
The connections between the vertices form a baseball diamond shape [3]. Project this system across the evolving cyber landscape, and we are able to derive a multidimensional picture of the underlying relationships between threat actors and their tools, techniques and processes.
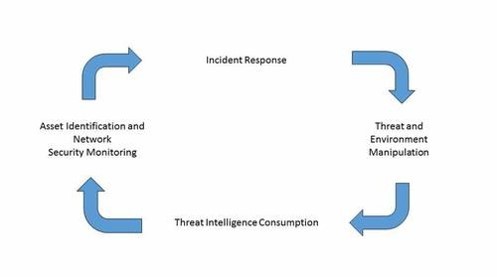
Active Cyber Defense Cycle
The active cyber defense cycle (ACDC) [4] consists of four phases that work together to maintain security, contributing to the safety and reliability of operations. The four phases are:
1) Asset identification and network security monitoring
2) Incident response
3) Threat and environment manipulation
4) Threat intelligence consumption.
Caveat
Cybersecurity models should not remain static forever; they are best regarded as pertaining to a moment of truth – this is in line with the unsteady state of cybersecurity [5]. They need to be reviewed and updated from time to time in relation in the input of threat intelligence.
References
[1] http://www.nist.gov/cyberframework/upload/cybersecurity-framework-021214.pdf
[2] https://www.sans.org/reading-room/whitepapers/analyst/killing-advanced-threats-tracks-intelligent-approach-attack-prevention-35302
[3] https://digital-forensics.sans.org/summit-archives/cti_summit2014/The_Diamond_Model_for_Intrusion_Analysis_A_Primer_Andy_Pendergast.pdf
[4] http://www.plantengineering.com/single-article/the-active-cyber-defense-cycle-a-strategy-to-ensure-oil-and-gas-infrastructure-cyber-security/01d9a9be2dc80a3d9a58b81c1ee8f213.html
[5] https://www.linkedin.com/pulse/unsteady-state-cybersecurity-freeman-ng?trk=mp-author-card