Protecting Intellectual Property: a Cybersecurity Perspective
Protecting Intellectual Property: a Cybersecurity Perspective
Intellectual property includes copyrights, trademarks, patents and trade secrets.
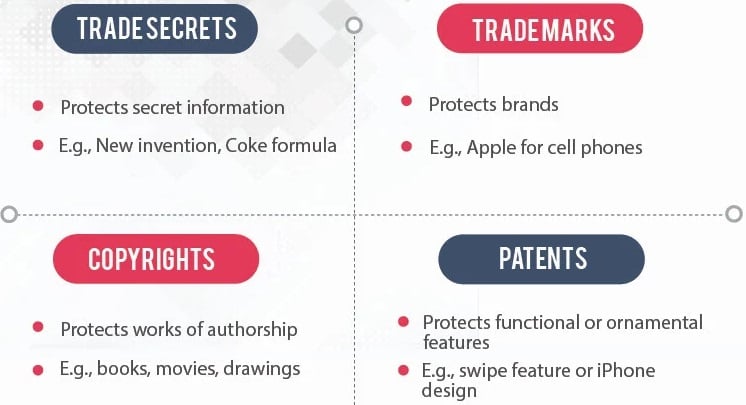
Intellectual property includes copyrights, trademarks, patents and trade secrets.

Advanced Persistent Threat (APT) is a kind of cyber attack. From organized cyber criminals to state-sponsored cyber actors, today’s APTs can bypass most security controls and cause serious damages to many organizations. A skilled and determined cyber criminal can use multiple vectors and entry points to navigate around defenses, breach network in minutes and evade detection for months. APTs present a challenge for various organizations. [1]
US National Institute of Standards and Technology (NIST) tells us that stopping all online crime is not a realistic goal, but simple steps can massively reduce the likelihood you’ll be the next victim. It’s simple: turn on MFA today! [1]
Because many of us have smartphones, the target on our backs is bigger than ever. Hackers, even nation states, are targeting smartphones to tap into cameras and microphones, but crucially and most of all, your data including your geo-location data.
The concept of “asymmetric threat” has its root from the military [1]. The asymmetric threat is defined as an attempt to circumvent or undermine an opponent’s strengths while exploiting the weakness, using methods that differ significantly from the opponent’s usual mode of operations.