Asymmetric Threats in Cybersecurity
Asymmetric Threat
The concept of “asymmetric threat” has its root from the military [1]. The asymmetric threat is defined as an attempt to circumvent or undermine an opponent’s strengths while exploiting the weakness, using methods that differ significantly from the opponent’s usual mode of operations.

If the concept is adapted to cybersecurity, then Asymmetric Threats in Cybersecuritydeal with cyber actors attempting to bypass the opponents’ defenses (firewalls, antivirus tools, intrusion detection systems, etc.) or undermine their strengths by exploiting their weakest links (human, technical weaknesses, etc.) through the use of methods, non-traditional tactics, or technologies that differ significantly from the other side.
Some examples of asymmetric threats in cybersecurity are as follows:
1) The encryption software, instead of protecting information’s confidentiality, is used to hinder the availability of information in the form of ransomware.
2) The Windows PowerShell scripts, which are part of Microsoft DNA, are used for hacking and exploiting computer systems. Thus, this tactic evades OS and antivirus defense mechanism.
In other words, asymmetric threats in cybersecurity are related to that thinking and actions differ significantly from cyber opponents in order to achieve the following by multi-folds:
* Maximize one’s own advantages;
* Exploit an opponent’s weaknesses;
* Attain the initiative, first-mover advantage; or
* Gain an absolute upper-hand.
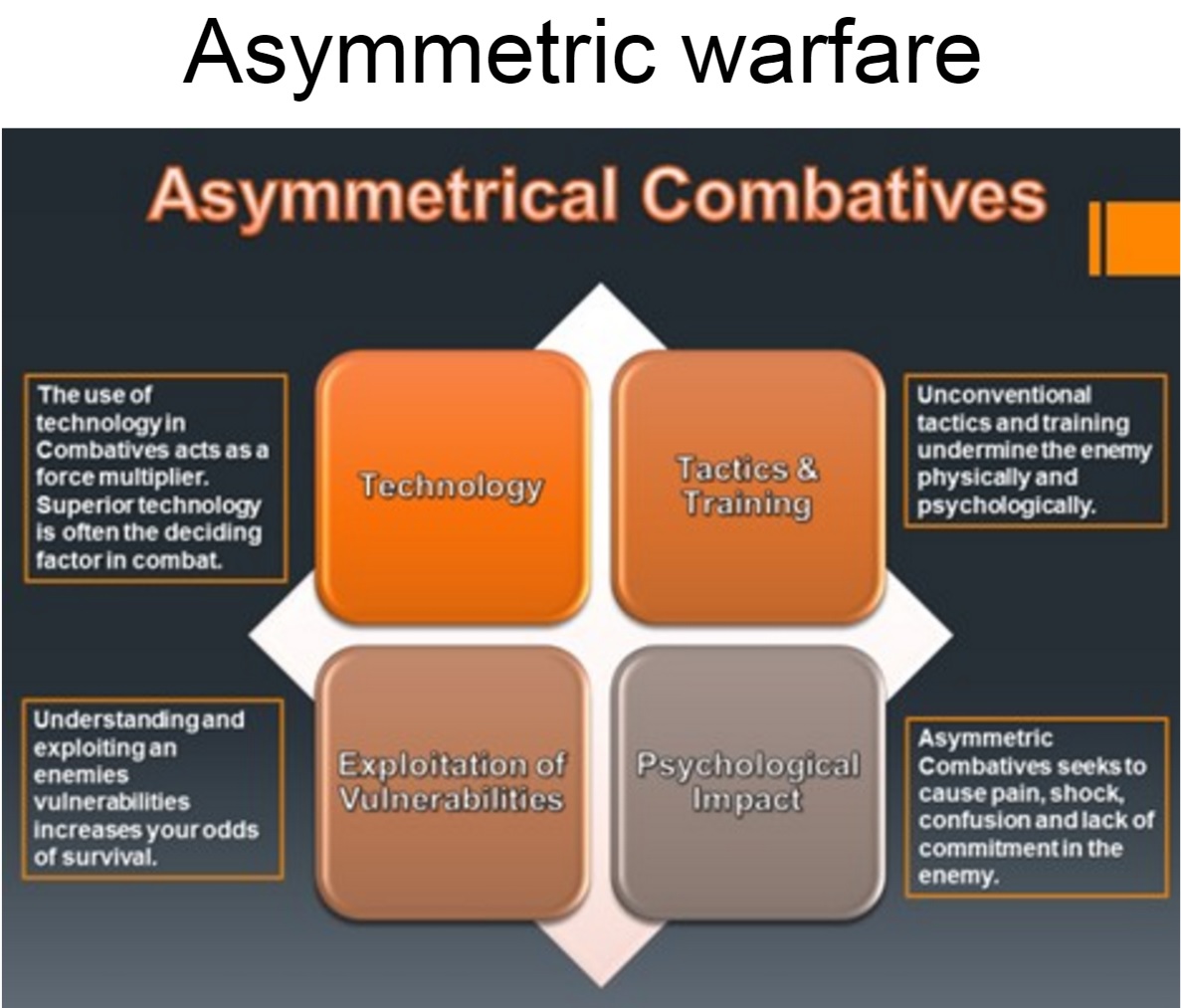
Back in the military arena, the asymmetrical threat will have an effect on warfare at three levels – strategic, operational, and tactical, but it will be most dramatic at the operational level [2]. The challenge for operational commanders will change most drastically. Those operational commanders who lead and fight in the battlefields and they have the responsibility for the defense of the country. It is pointed out that most leaders at strategic, operational, and tactical levels are ill prepared for asymmetrical warfare that now seem to be more of a probability than a possibility.

Conclusion
A close parallel in cybersecurity: business leaders, information security officers, and IT administrators are less prepared or trained to face asymmetrical threats in cybersecurity. The information security officers, as the operational commanders in cybersecurity defending the business organisations, face the bulk of the pressure. The gap in the capabilities of cyber attack and cyber defense is growing, rather than narrowing.
References
[1] Campbell, LTG Kevin, “Asymmetrical Threats: a vital relevancy for information operations”, Army Space Journal, P. 4, 2007 Winter Edition
[2] Nemeth, Jozsef, “A new security problem: the asymmetrical warfare”, a PhD thesis, Miklos Zrinyi National Defence University at Budapest of Hungary. Retrieved on 2 May 2017 at http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.604.7260&rep=rep1&type=pdf

