The Unsteady State of Cybersecurity
The State of Cybersecurity
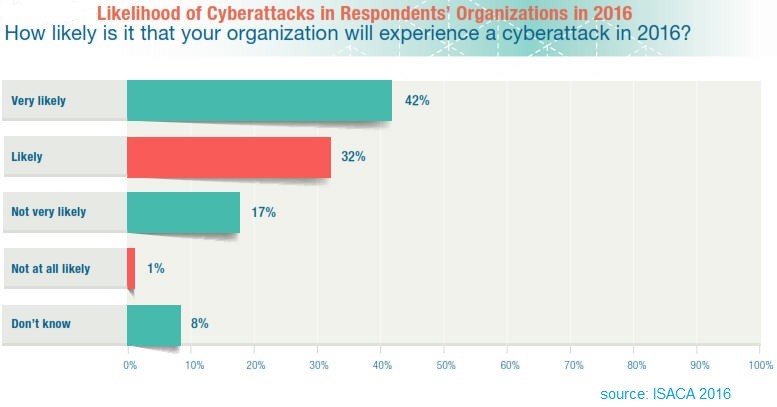
In November and December 2015, ISACA and RSA Conference conducted a global survey of 461 cybersecurity managers and practitioners [1]. Survey participants confirmed that the number of breaches targeting organizational and individual data continues to go unchecked and the sophistication of attack methodologies is evolving. The current state of global cybersecurity remains chaotic, the attacks are not expected to slow down, and almost 75 percent of respondents expect to fall prey to a cyberattack in 2016. Cybercriminals are the most prevalent attackers and continue to employ social engineering as their primary initial attack vector.
The Unsteady State of Cybersecurity
In cybersecurity, an IT system or a process is in a steady state if and only if the variables (called state variables) which define the behavior of the system or the process are unchanging in time. In continuous time, this means that for those properties p of the system, the partial derivative with respect to time (t) is zero and remains so:
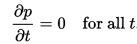
In many systems, a steady state is not achieved until sometime after the system is started or initiated. This initial situation is often identified as a transient state, start-up or warm-up period.
The concept of a steady state has relevance in many fields, in particular thermodynamics and engineering. If a system is in a steady state, then the recently observed behavior of the system will continue into the future. In stochastic systems, the probabilities that various states will be repeated will remain constant.
Are We in Unsteady State of Cybersecurity?
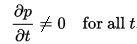
We are asking whether those properties p of the IT ecosystem change over time. More fundamentally are the security features of firewall adequate over time? Are the security features of endpoint protection adequate over time? Are the prevailing security models and principles (defense in depth, least privilege, etc.) adequate over time?
Security Bypassing Techniques
There are articles in Network World [2] and Defcon [3] that describe bypassing firewalls, application whitelists, and antivirus solutions in 20 seconds.
Malware Obfuscation Techniques
Malicious software (malware) can survive by hiding beyond the radar of anti-malware solutions through a combination of and / or a mutation of techniques like encryption, polymorphism, and so on. Obfuscation is a technique that makes binary and textual data unreadable and/or hard to understand. The number of malware obfuscation techniques is growing rapidly; this renders traditional anti-malware solutions very inadequate.
So far, in 2010, some antivirus (AV) vendors claim to be seeing upwards of 55,000 new malware samples a day! To put this in perspective, in order to obtain blanket signature coverage, a vendor would have 1.6 seconds to analyze a new malware strain, generate a new signature and push it out to their entire customer base’s scanner databases. And this would need to happen 24 hours a day, 7 days a week. As is already the trend, to combat modern malware threats, AV vendors will employ an array of techniques ranging from simple pattern matching culminating in advanced heuristic analysis. There will likely be less scanning of files looking for signatures (although this will still play an important role) and more event-driven algorithmic detection methods. Refer to the following Cisco’s articles for more details [4] & [5].
Exploitation Techniques
We have witnessed exploitation techniques evolving at rapid pace. Below the statistics emerged from the Talos’s study [6] that confirm the strategic role of the exploit kits in the criminal ecosystem:
90,000 Targeted Victims Per Day
9,000 Exploits Served Per Day
3,600 (40%) Systems Successfully Compromised
2,232 (62%) Angler Infections Delivered Ransomware
2.9% (Based on USCert via Symantec) Ransoms Paid Daily
$300 Average Ransom Demanded
147 Total Redirection Servers
64.73 Ransoms Paid Daily
$19,419.00 Daily Ransom Revenue Per Server
$95,153.10 Gross Daily Ransom Revenue
$2,854,593.00 Gross Monthly Ransom Revenue
$34,225,116.00 Gross Annual Ransom Revenue
Security Principles under Challenge
Apart from cybersecurity tools under challenges cybersecurity principles do not immune themselves. Defense in Depth is a must-know security principle for education and examination. The technological developments in cloud, smartphones, Internet of Things, etc. render the layered fortification more and more insufficient for cyber defense [7] & [8].
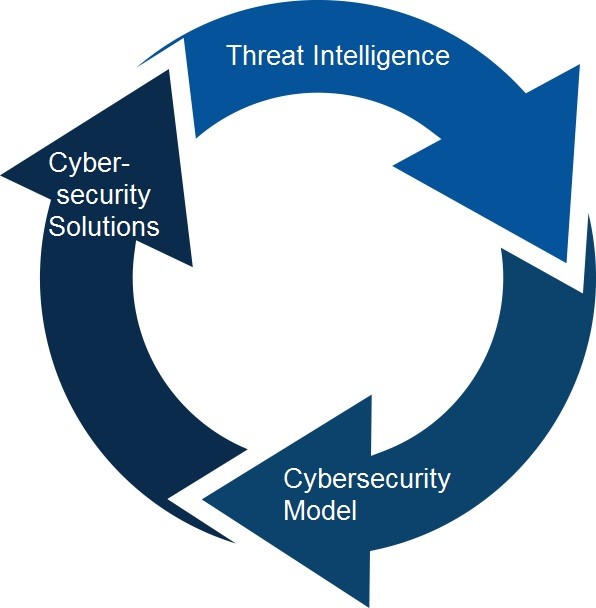
Dynamic and Proactive Cybersecurity
The hope lies in more open and easy-to-access threat intelligence sharing and timely updates on cybersecurity models, principles and solutions [9] & [10]. Cybersecurity is not an ivory tower exercise nor a propaganda tool; we need more collaborative and proactive approach.
References
[1] http://www.isaca.org/cyber/pages/state-of-cybersecurity-implications-for-2016.aspx
[2] http://www.networkworld.com/article/2601300/microsoft-subnet/bypassing-hardware-firewalls-in-20-seconds.html
[3] https://defcon.org/images/defcon-22/dc-22-presentations/Balazs/DEFCON-22-Zoltan-Balazs-Bypass-firewalls-application-whitelists-in-20-seconds-UPDATED.pdf
[4] http://blogs.cisco.com/security/a_brief_history_of_malware_obfuscation_part_1_of_2
[5] http://blogs.cisco.com/security/a_brief_history_of_malware_obfuscation_part_2_of_2
[6] http://resources.infosecinstitute.com/the-threatening-evolution-of-exploit-kits/
[7] http://www.infosecisland.com/blogview/19373-The-Myth-of-Defense-in-Depth.html
[8] http://blog.vlcmtech.com/blog/study-shows-most-defense-in-depth-security-is-inadequate
[9] https://www.gartner.com/imagesrv/media-products/pdf/webroot/issue1_webroot.pdf
[10] http://www.govtech.com/dc/articles/Cybersecurity-Taking-a-Proactive-Approach-is-Key.html

